With the API's there are a lot of different ways of authenticating. As Deployteq is more and more getting compatible with all different kinds of API's and has more and more standard ways of integrating, more ways of authentication are needed. The authentication with certificates is one of them.
Within this documentation we assume you know the basics of signing API requests with certificates. We only wil describe how you can use them within Deployteq.
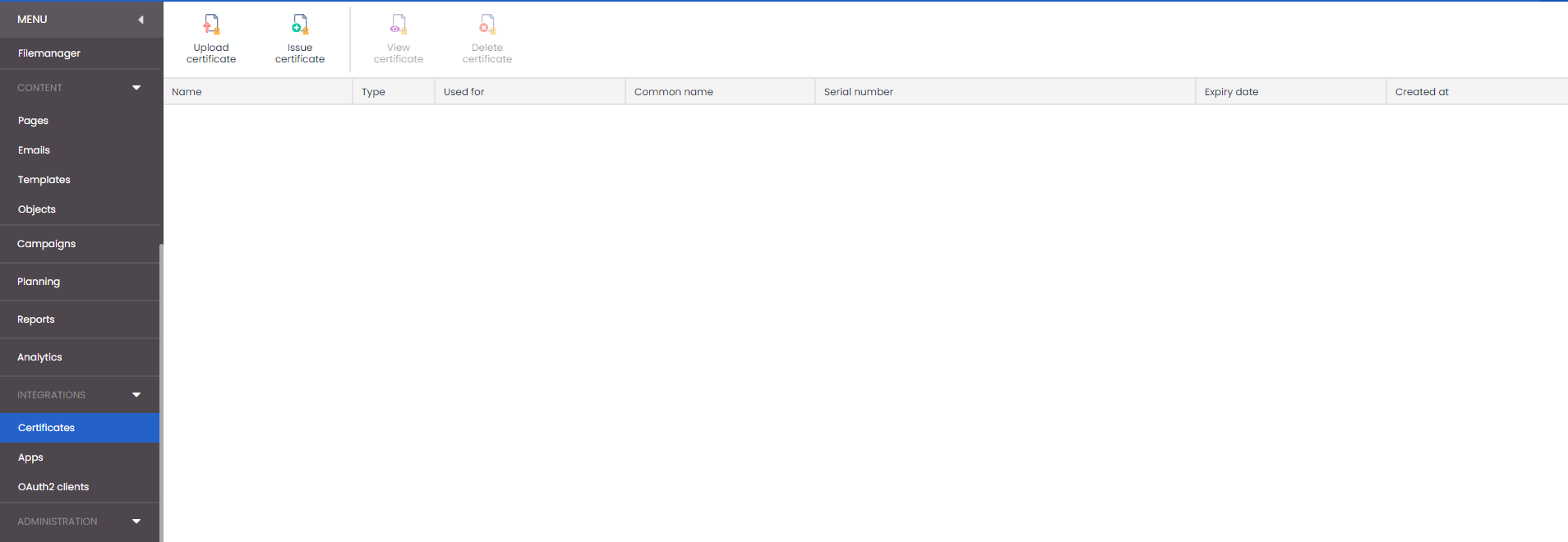
Certificate manager
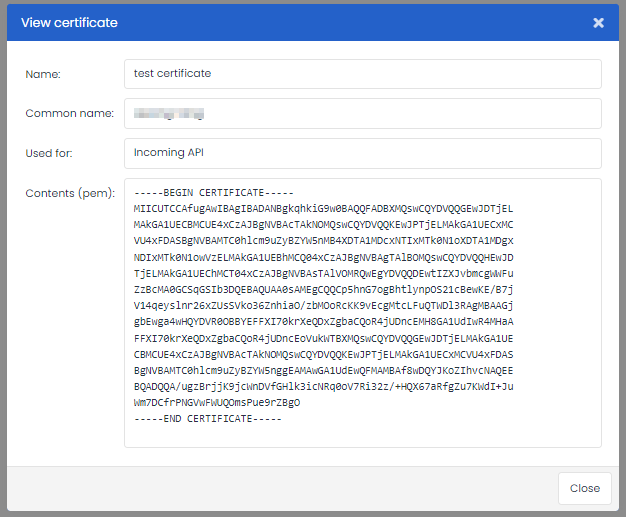
First of all we have created an interface within Deployteq where you can manage your own certificates. These certificates will be made available in different integrations and API apps, like the webhooks and PEGA. Always give the certificates a clear name, so you know which one to use within the other modules in Deployteq.
Type of certificates
There are two different certificates in Deployteq
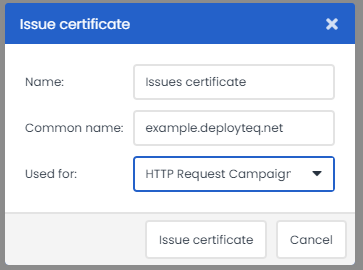
1. Issued certificates
Deployteq can issue self signed certificates for a certain domain. What you will get, is the public certificate for the client certificate which you can install in the application of the third party. The third party can validate the request with Deployteq to make sure the call is coming is really coming from Deployteq. The issued certificates will automatically have a life span of 1 year. You will receive the public certificate to implement with the third party. The common name can be *.myclang.com and *.clang.cloud, so for example api.company.com
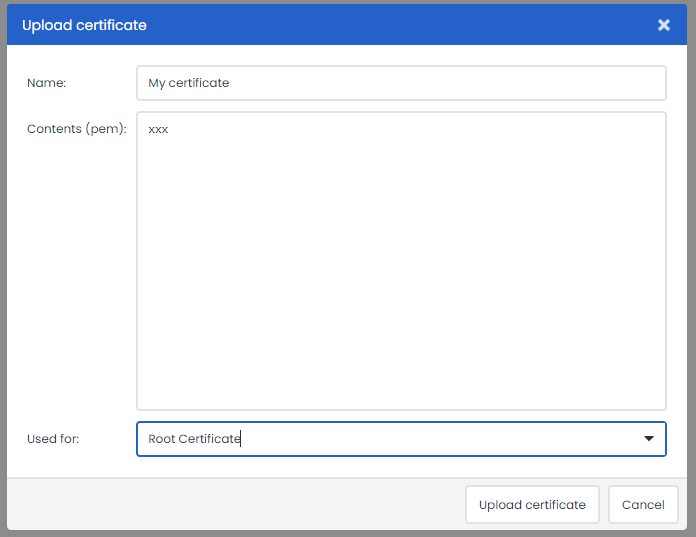
2. Uploaded certificates
When there are incoming calls to the webhook, you can upload the certificate within Deployteq with the upload. You will see a screen where you again can give the certificate a clear name again and paste the certificate as text in Deployteq. Later you can use this certificate within incoming API's like the webhook, where we can verify the call with this certificate.
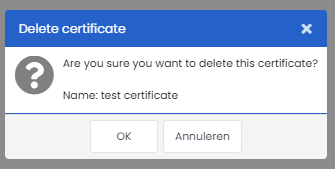
Expired certificates
Once a certificate is expired or you want to revoke access to Deployteq with a certain certificate, you can simply delete the certificate in the manager and the connection based on the certificate will not be available anymore
Public certificates
Lastly you can view the public certificates, for example for checking if it matches the one in your connected application or to get it for your third party at a later time.
Using certificates with outgoing integrations
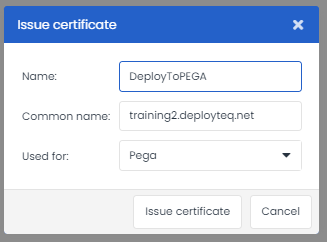
The first outgoing integration we now have is PEGA. When you issue a certificate, you can now select for which app you want to use the certificate for.
This can take up to 10 minutes to work correctly for the next call.
The app will use the first valid certificate that is in the certificate manager. In the PEGA app you can add an endpoint and username password. This will be the fallback at the moment the certificate is not valid or deleted.
Using certificates with webhooks
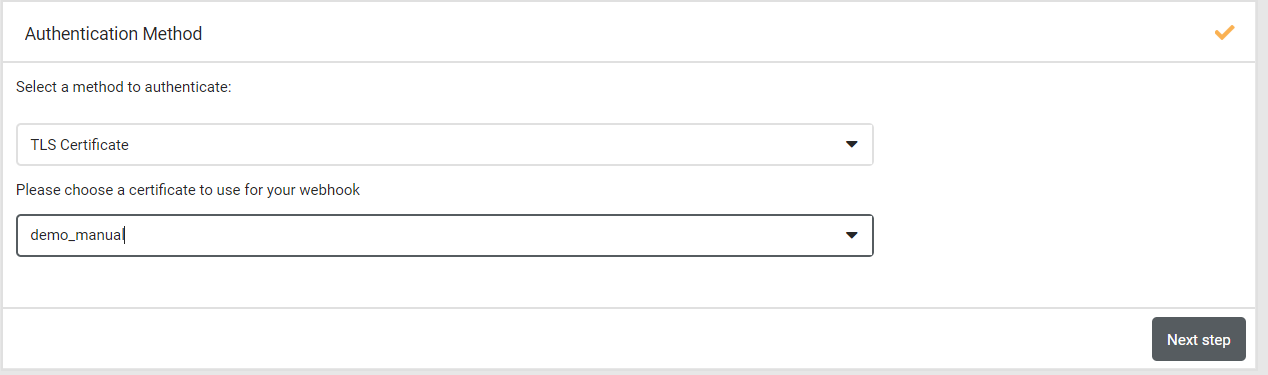
When you want to use an uploaded certificate for a specific webhook, you can select this when creating the webhook. When you've given your webhook a name and you have an uploaded certificate ready in the certificate manager, you will see the question, do you want to use a client certificate to validate the request. If you check this, you will get a dropdown where you can select one of the uploaded certificates.