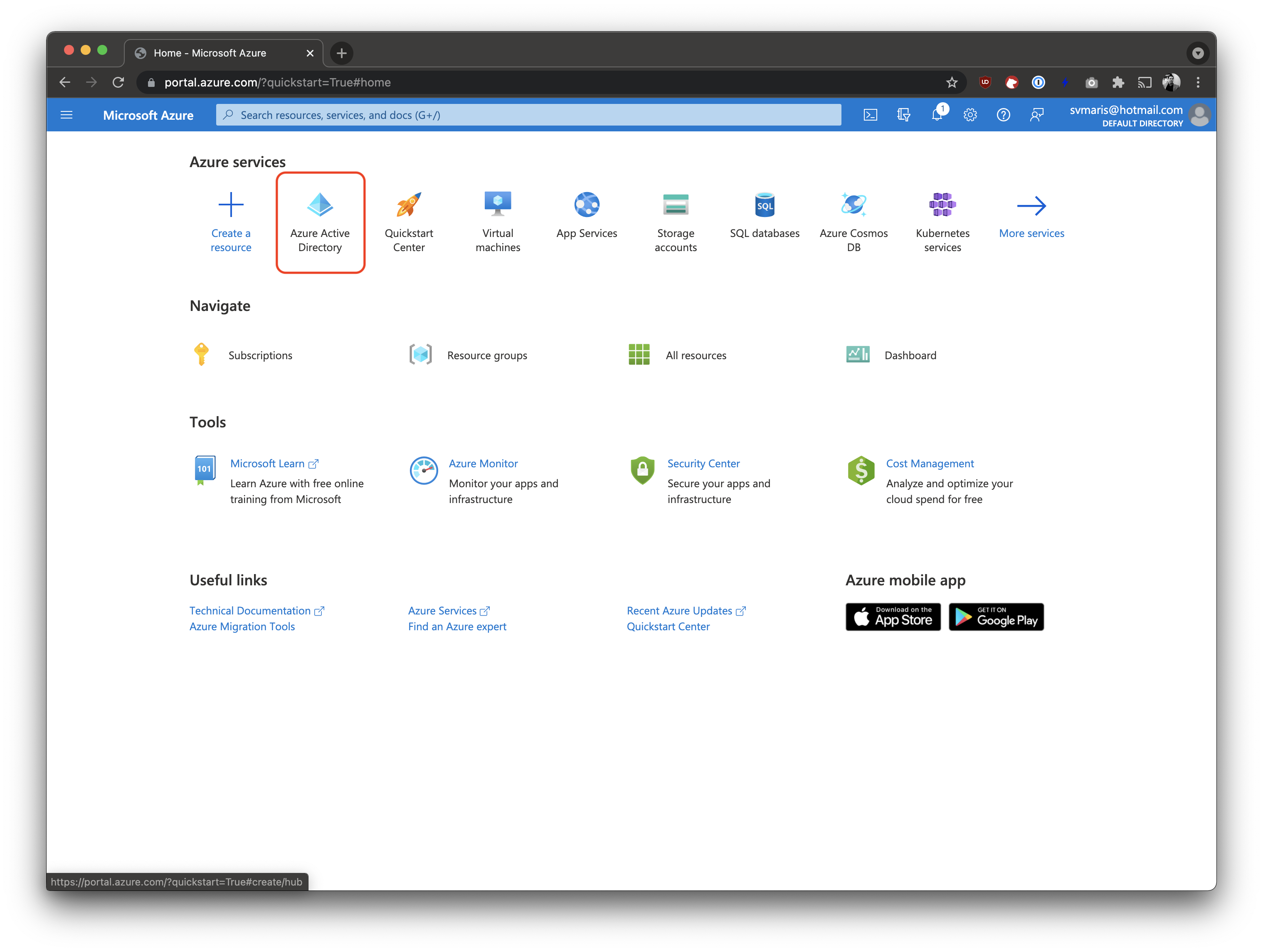
Go to the Azure Active Directory console
Click it on the main screen, or search for it using the search bar at the top.
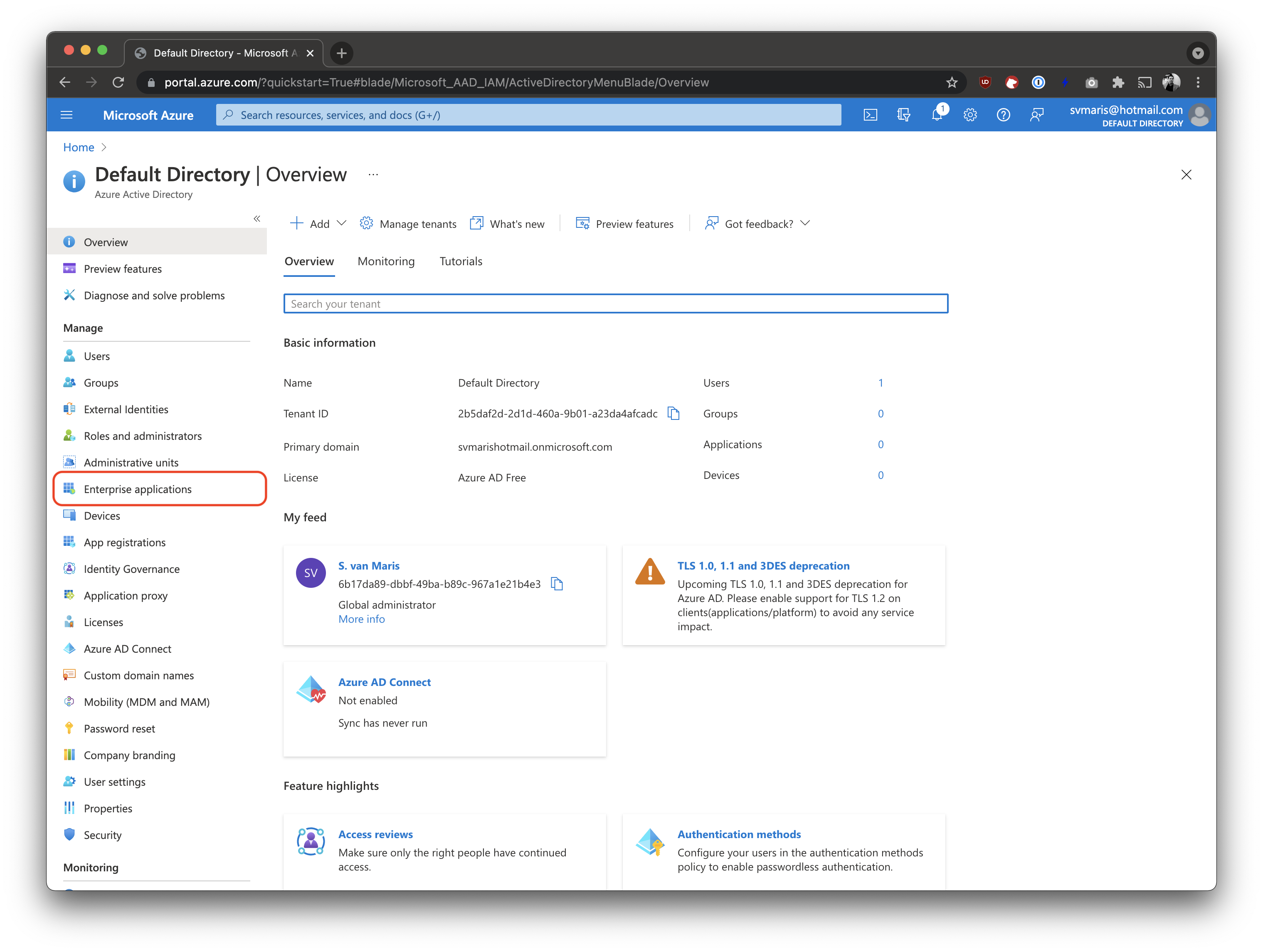
Click on "Enterprise applications"
In the AAD console, click on Enterprise applications in the main menu
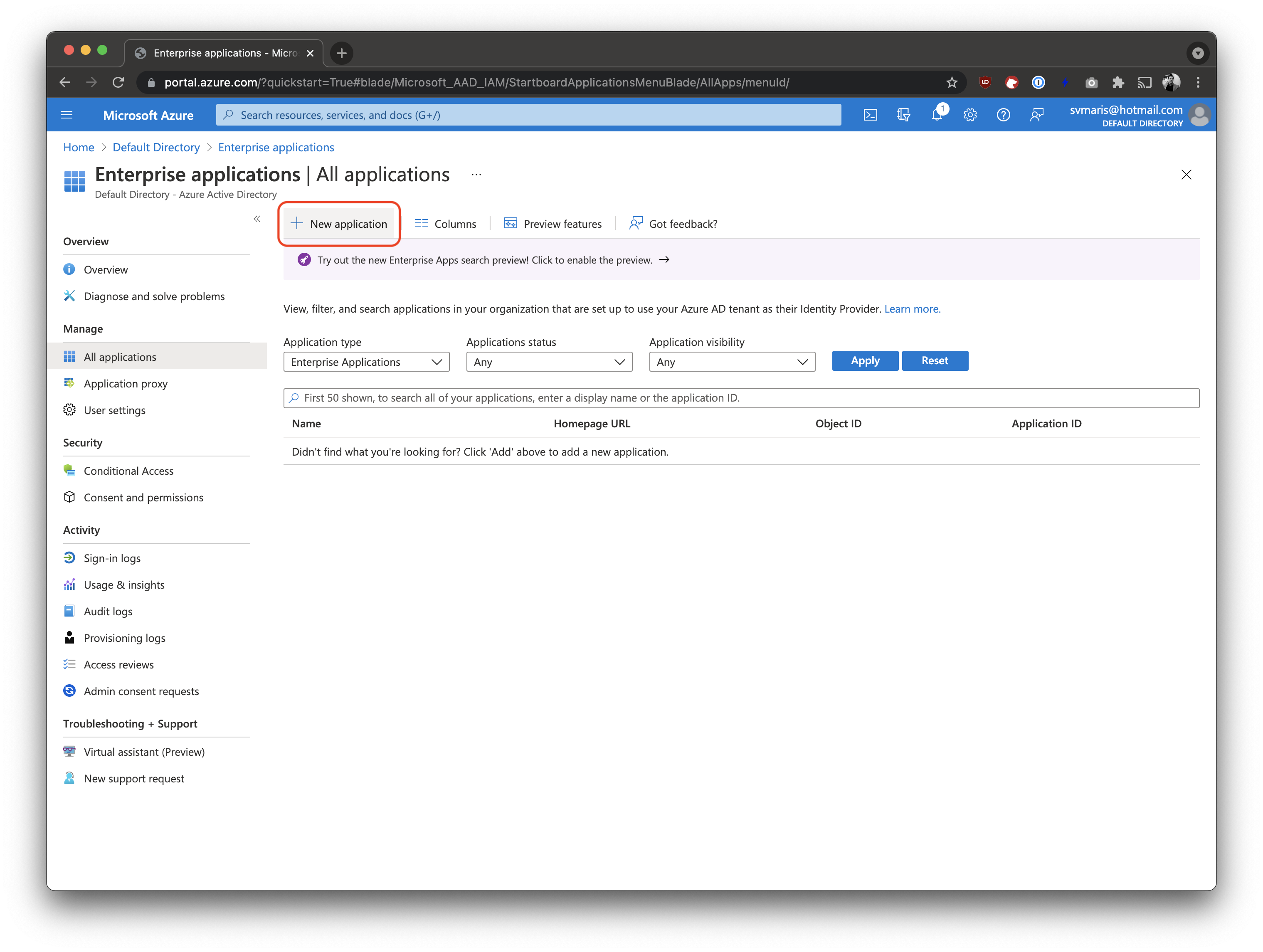
Create a new Application
Click on New application
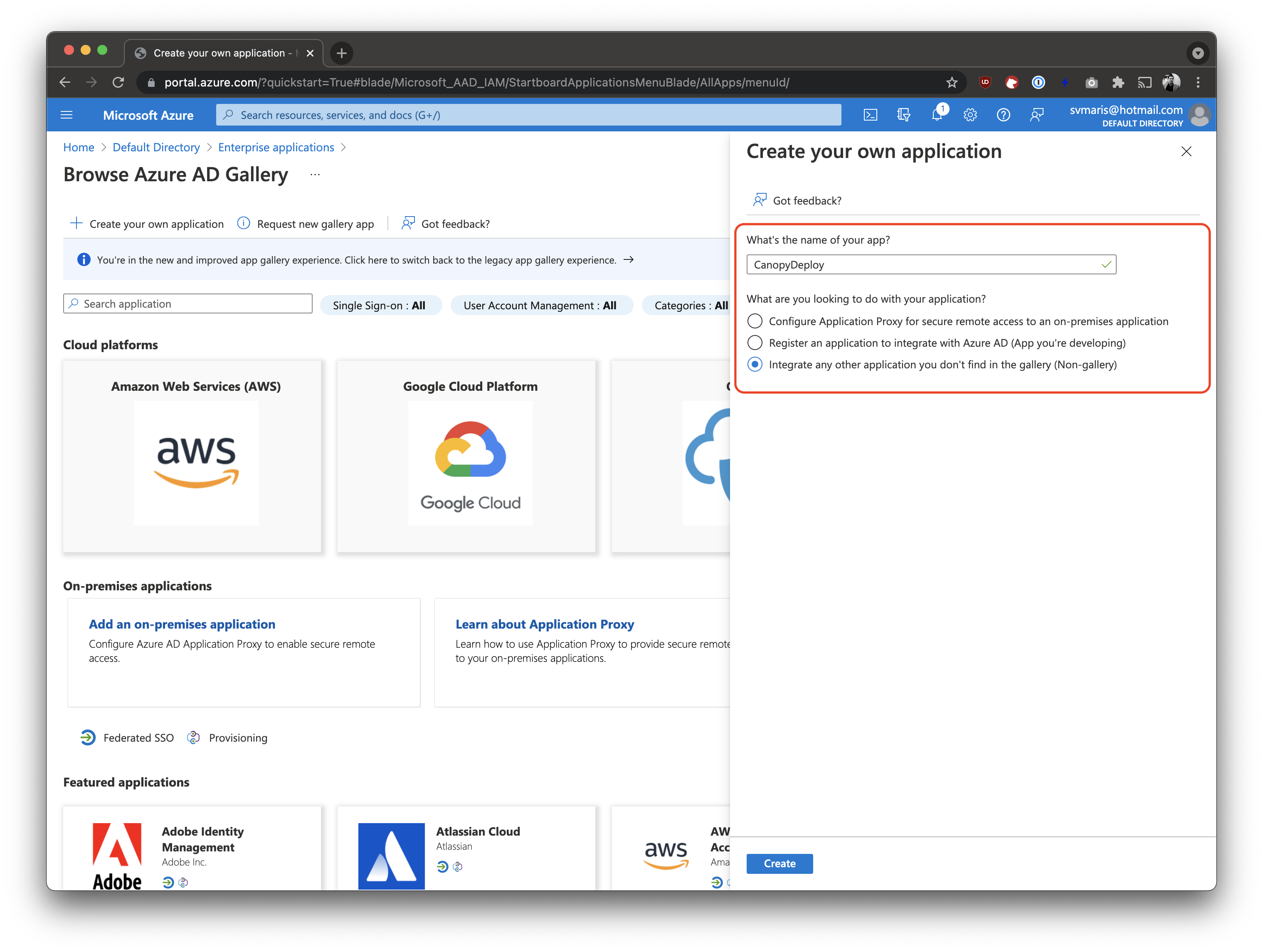
And then click Create your own application
Fill out the form. Please make sure to select the Integrate any other application you don't find in the gallery (Non-gallery) option.
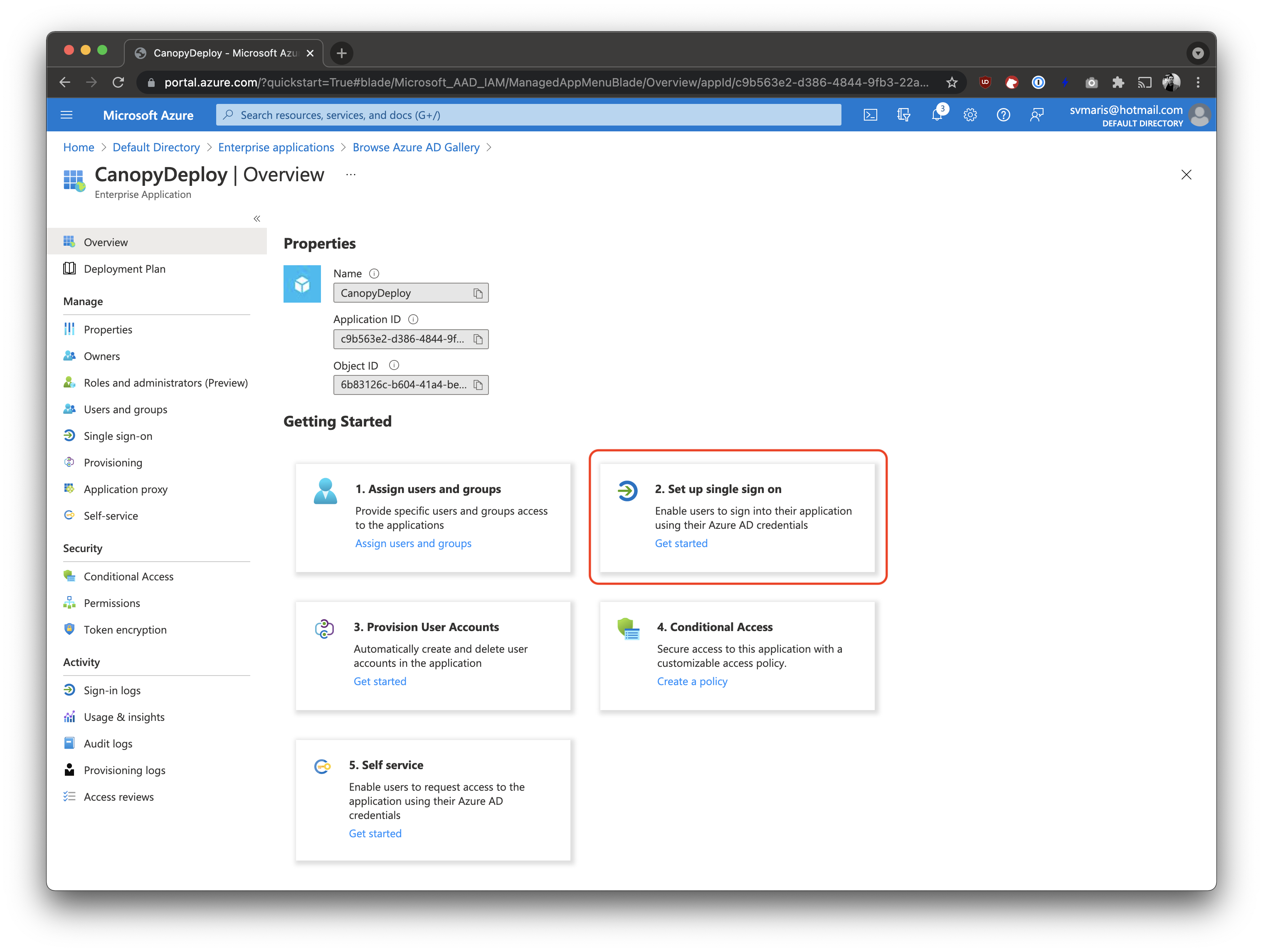
Set up single sign on with SAML
After creating the new application, click on 2. Set up single sign on.
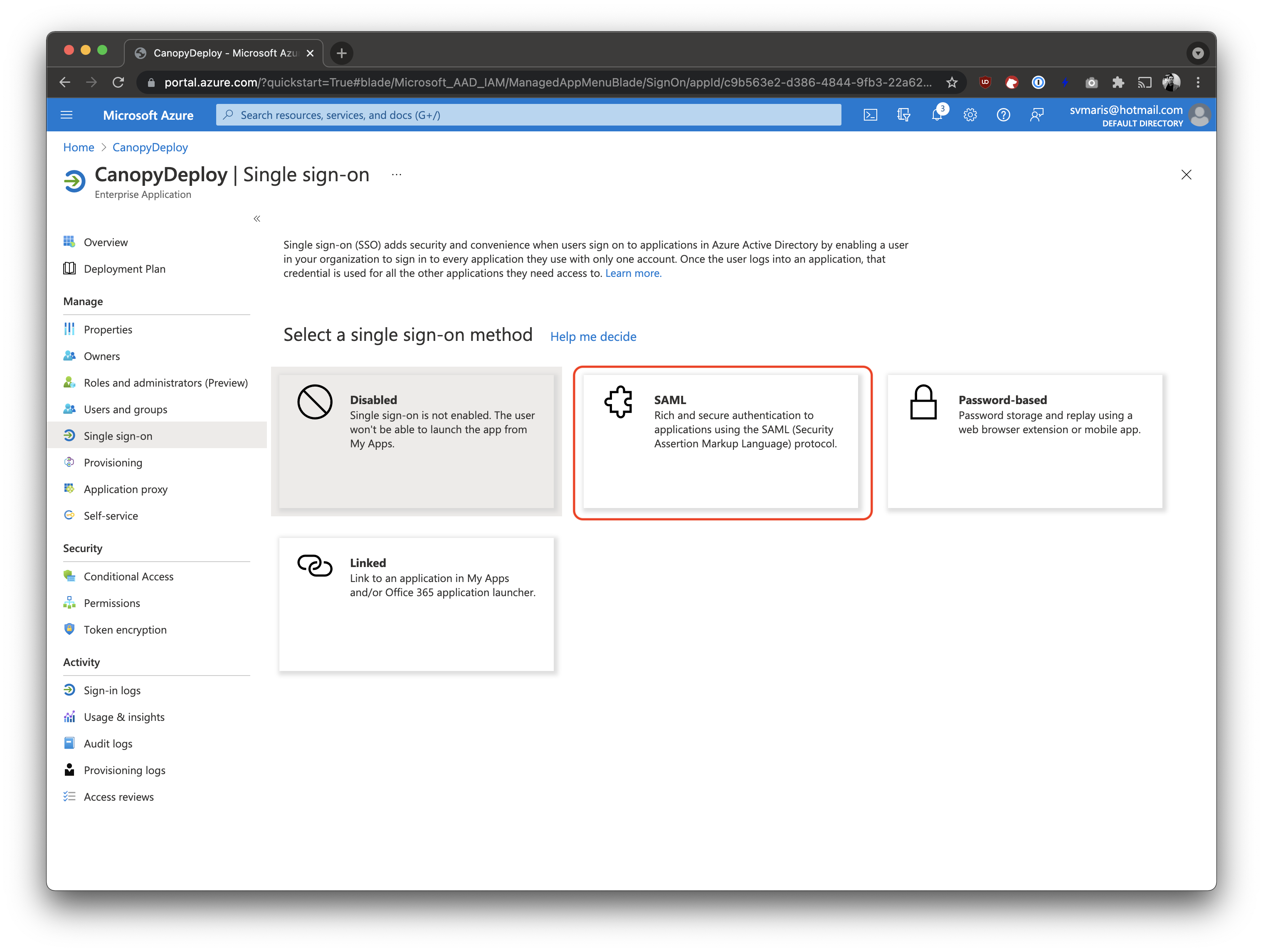
Then select SAML.
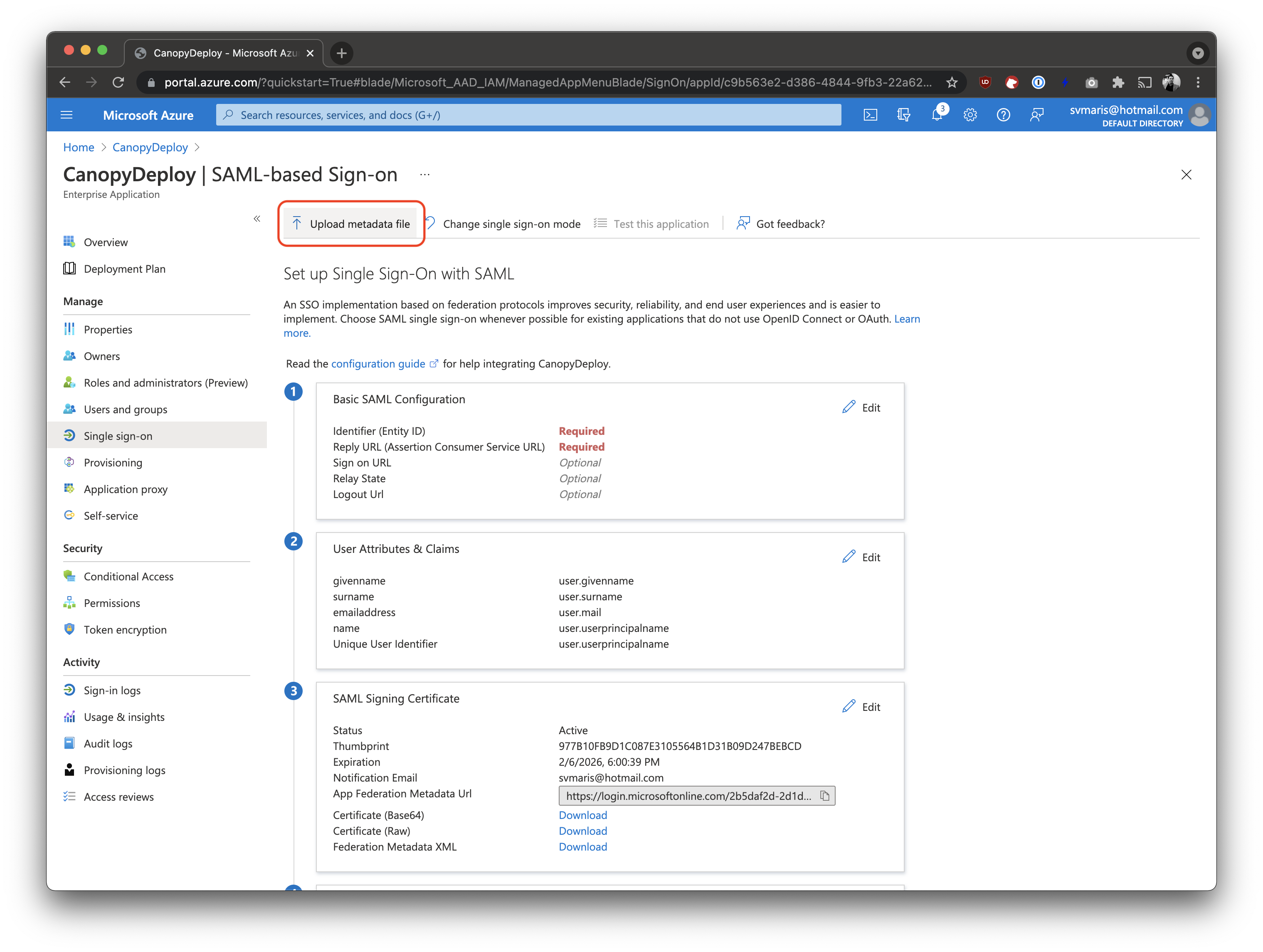
Save the following XML (or download here) to a file and upload it to Azure Active Directory using the Upload metadata file button.
<?xml version="1.0"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" entityID="https://deployteq.net">
<md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol urn:oasis:names:tc:SAML:1.1:protocol">
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIIEcjCCAtoCCQC8BLma3E3YizANBgkqhkiG9w0BAQsFADB7MQswCQYDVQQGEwJOTDEQMA4GA1UECAwHVVRSRUNIVDEXMBUGA1UEBwwOSHVpcyB0ZXIgSGVpZGUxEDAOBgNVBAoMB1RlYW1JVEcxDzANBgNVBAsMBkRldm9wczEeMBwGA1UEAwwVYXV0aC5jYW5vcHlkZXBsb3kubmV0MB4XDTIxMDIyNDA2MzQ1MloXDTMxMDIyNDA2MzQ1MlowezELMAkGA1UEBhMCTkwxEDAOBgNVBAgMB1VUUkVDSFQxFzAVBgNVBAcMDkh1aXMgdGVyIEhlaWRlMRAwDgYDVQQKDAdUZWFtSVRHMQ8wDQYDVQQLDAZEZXZvcHMxHjAcBgNVBAMMFWF1dGguY2Fub3B5ZGVwbG95Lm5ldDCCAaIwDQYJKoZIhvcNAQEBBQADggGPADCCAYoCggGBAN8BIsaRvWnijN350i0V2ldZmjg7o/huoXR6qfJil1BfzwSYIn6ky8lFDmD+kcpdcG+lCpELM6u72I+dvDS8heZOWhQxFQGlgMwbMgkOJS+y5pBf5EG4CRoo0tl8ASd0XrmH/+wdHX0jPYa/anp5b3FC2Sq5L00FaAK4V3/KqQtDxedR1c5zfleBqZ2lgwg83U+TARZajLXWXAbWUFt8cC1zF8gdaAPjcIjJpAZIyk4uTKATw9L/u/gS6j+kJdvKWbtqQcmSO5d9wUicJm7BJrhoJYF+fvuYxn1Ci7vW5JzmzcbL7P1V2qtRRlq8k0zdGD+QWjRSkQpiSDciR9LD01yCLMDEl8LBii8Dg2fpMtQdAyqrJVAPXgeG6tU3gFheoZmljSbR7wmJFiz5JFkySPbS8AlJveerRClb3PYG3VlIpKHCleRZm0xgM2TGnqO2/6mUN7oijJ0QRDb3Lj24Q0uDqqgYdE1O9tpNmjt3wKQc5JbgHS+ME4Txu1EdomPjXwIDAQABMA0GCSqGSIb3DQEBCwUAA4IBgQCMmv1qKoBEg2WdECGLTe2XTYJxJInv8n72VoOk9agsmPm3L7MDsNz4NRB/0GH1IZ7RW8On6NA8Aw4O7odhuqTrITsLos/okpP1ermdFioBnhYD9OUoU2KBX4rldBmLOyGFFzjjHm+6s3t/xaep8hHEbFcqdOHVKn81DErqTkFeSux8LcnzxEPGGh6v68E5vDKcnwmiuTmUi1wC+0II0V0yXOWKBMy7bjBxnvHWE7kp1X6PE6ugNmHoCmg7Tx648v9y4IviaWdUSNNVKMAX09iFrzIko+98dK77L4NjUZhjiI0DkATOS2E9SjodnNZGxANnk6DxEWMeUY6IGFVQCeTtdQZ/P5dHAEoP1l6jDWAw0mE5yqsBasWoUdK2FkqjEsxkKzyA2uWIdPQPwVvUmyKtvbKBKwDXOrOyxfo/RL3KB/3Bef2NsPLb42SlB2rGhUziSvXc/7xDF899N/E6IEHfIH16i4ANjbrGm8t3X7Qk/KNUuGtyV+RObVdEqxki5M8=</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:X509Data>
<ds:X509Certificate>MIIEcjCCAtoCCQC8BLma3E3YizANBgkqhkiG9w0BAQsFADB7MQswCQYDVQQGEwJOTDEQMA4GA1UECAwHVVRSRUNIVDEXMBUGA1UEBwwOSHVpcyB0ZXIgSGVpZGUxEDAOBgNVBAoMB1RlYW1JVEcxDzANBgNVBAsMBkRldm9wczEeMBwGA1UEAwwVYXV0aC5jYW5vcHlkZXBsb3kubmV0MB4XDTIxMDIyNDA2MzQ1MloXDTMxMDIyNDA2MzQ1MlowezELMAkGA1UEBhMCTkwxEDAOBgNVBAgMB1VUUkVDSFQxFzAVBgNVBAcMDkh1aXMgdGVyIEhlaWRlMRAwDgYDVQQKDAdUZWFtSVRHMQ8wDQYDVQQLDAZEZXZvcHMxHjAcBgNVBAMMFWF1dGguY2Fub3B5ZGVwbG95Lm5ldDCCAaIwDQYJKoZIhvcNAQEBBQADggGPADCCAYoCggGBAN8BIsaRvWnijN350i0V2ldZmjg7o/huoXR6qfJil1BfzwSYIn6ky8lFDmD+kcpdcG+lCpELM6u72I+dvDS8heZOWhQxFQGlgMwbMgkOJS+y5pBf5EG4CRoo0tl8ASd0XrmH/+wdHX0jPYa/anp5b3FC2Sq5L00FaAK4V3/KqQtDxedR1c5zfleBqZ2lgwg83U+TARZajLXWXAbWUFt8cC1zF8gdaAPjcIjJpAZIyk4uTKATw9L/u/gS6j+kJdvKWbtqQcmSO5d9wUicJm7BJrhoJYF+fvuYxn1Ci7vW5JzmzcbL7P1V2qtRRlq8k0zdGD+QWjRSkQpiSDciR9LD01yCLMDEl8LBii8Dg2fpMtQdAyqrJVAPXgeG6tU3gFheoZmljSbR7wmJFiz5JFkySPbS8AlJveerRClb3PYG3VlIpKHCleRZm0xgM2TGnqO2/6mUN7oijJ0QRDb3Lj24Q0uDqqgYdE1O9tpNmjt3wKQc5JbgHS+ME4Txu1EdomPjXwIDAQABMA0GCSqGSIb3DQEBCwUAA4IBgQCMmv1qKoBEg2WdECGLTe2XTYJxJInv8n72VoOk9agsmPm3L7MDsNz4NRB/0GH1IZ7RW8On6NA8Aw4O7odhuqTrITsLos/okpP1ermdFioBnhYD9OUoU2KBX4rldBmLOyGFFzjjHm+6s3t/xaep8hHEbFcqdOHVKn81DErqTkFeSux8LcnzxEPGGh6v68E5vDKcnwmiuTmUi1wC+0II0V0yXOWKBMy7bjBxnvHWE7kp1X6PE6ugNmHoCmg7Tx648v9y4IviaWdUSNNVKMAX09iFrzIko+98dK77L4NjUZhjiI0DkATOS2E9SjodnNZGxANnk6DxEWMeUY6IGFVQCeTtdQZ/P5dHAEoP1l6jDWAw0mE5yqsBasWoUdK2FkqjEsxkKzyA2uWIdPQPwVvUmyKtvbKBKwDXOrOyxfo/RL3KB/3Bef2NsPLb42SlB2rGhUziSvXc/7xDF899N/E6IEHfIH16i4ANjbrGm8t3X7Qk/KNUuGtyV+RObVdEqxki5M8=</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://auth.deployteq.net/saml2.0/signout.php"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://auth.deployteq.net/saml2.0/signout.php"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://auth.deployteq.net/saml2.0/module.php/saml/sp/saml2-acs.php/deployteq" index="0"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:1.0:profiles:browser-post" Location="https://auth.deployteq.net/saml2.0/module.php/saml/sp/saml1-acs.php/deployteq" index="1"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://auth.deployteq.net/saml2.0/module.php/saml/sp/saml2-acs.php/deployteq" index="2"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:1.0:profiles:artifact-01" Location="https://auth.deployteq.net/saml2.0/module.php/saml/sp/saml1-acs.php/deployteq/artifact" index="3"/>
</md:SPSSODescriptor>
<md:ContactPerson contactType="technical">
<md:GivenName>Devops</md:GivenName>
<md:EmailAddress>mailto:devops@deployteq.com</md:EmailAddress>
</md:ContactPerson>
</md:EntityDescriptor>
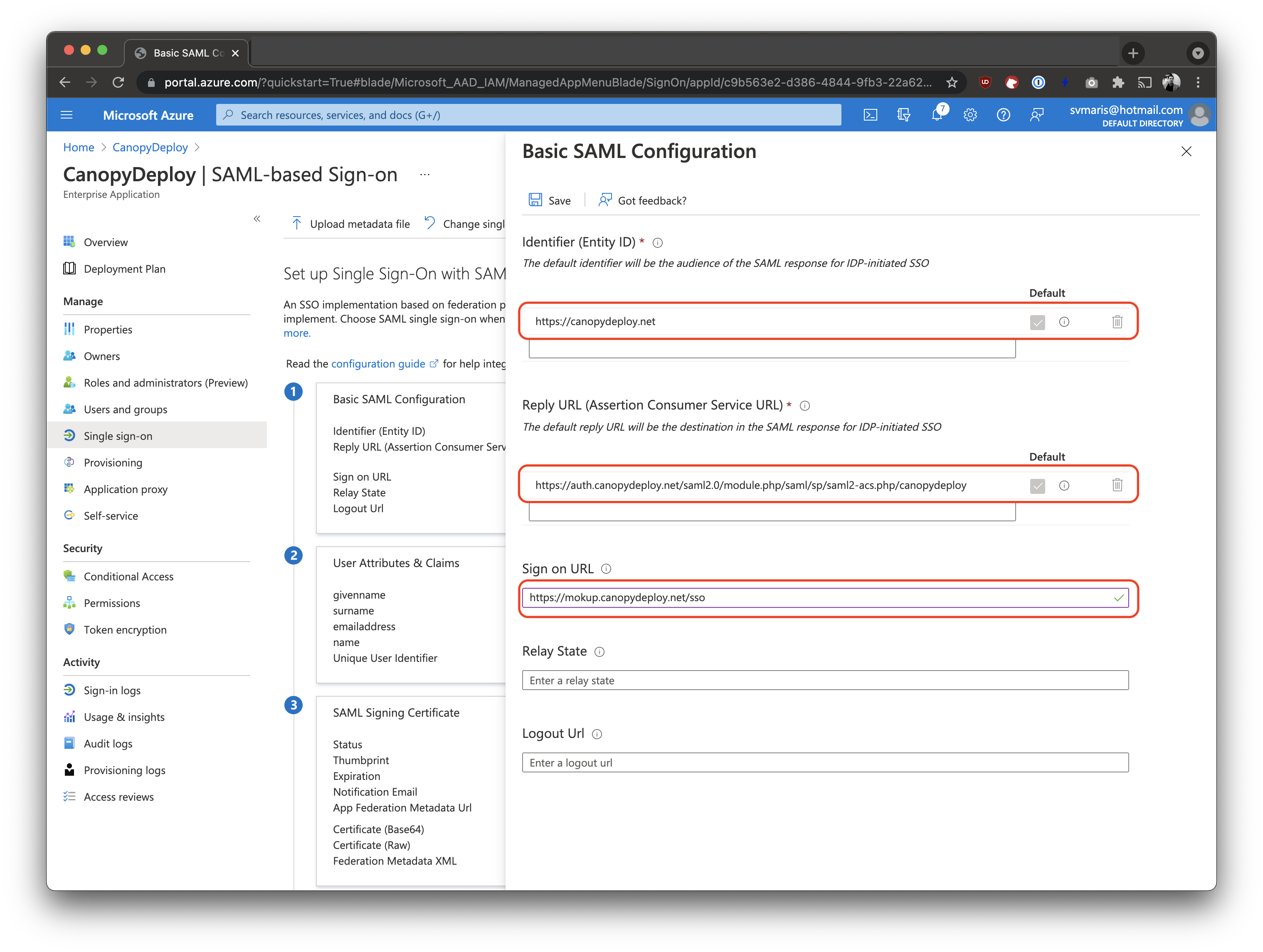
After uploading the file, configure the following items:
- Identifier (Entity ID): Replace the default value with https://deployteq.net
- URL: Set this to https://auth.deployteq.net/saml2.0/module.php/saml/sp/saml2-acs.php/deployteq
- Sign on URL: Set this to https://<portal name>.deployteq.net/sso
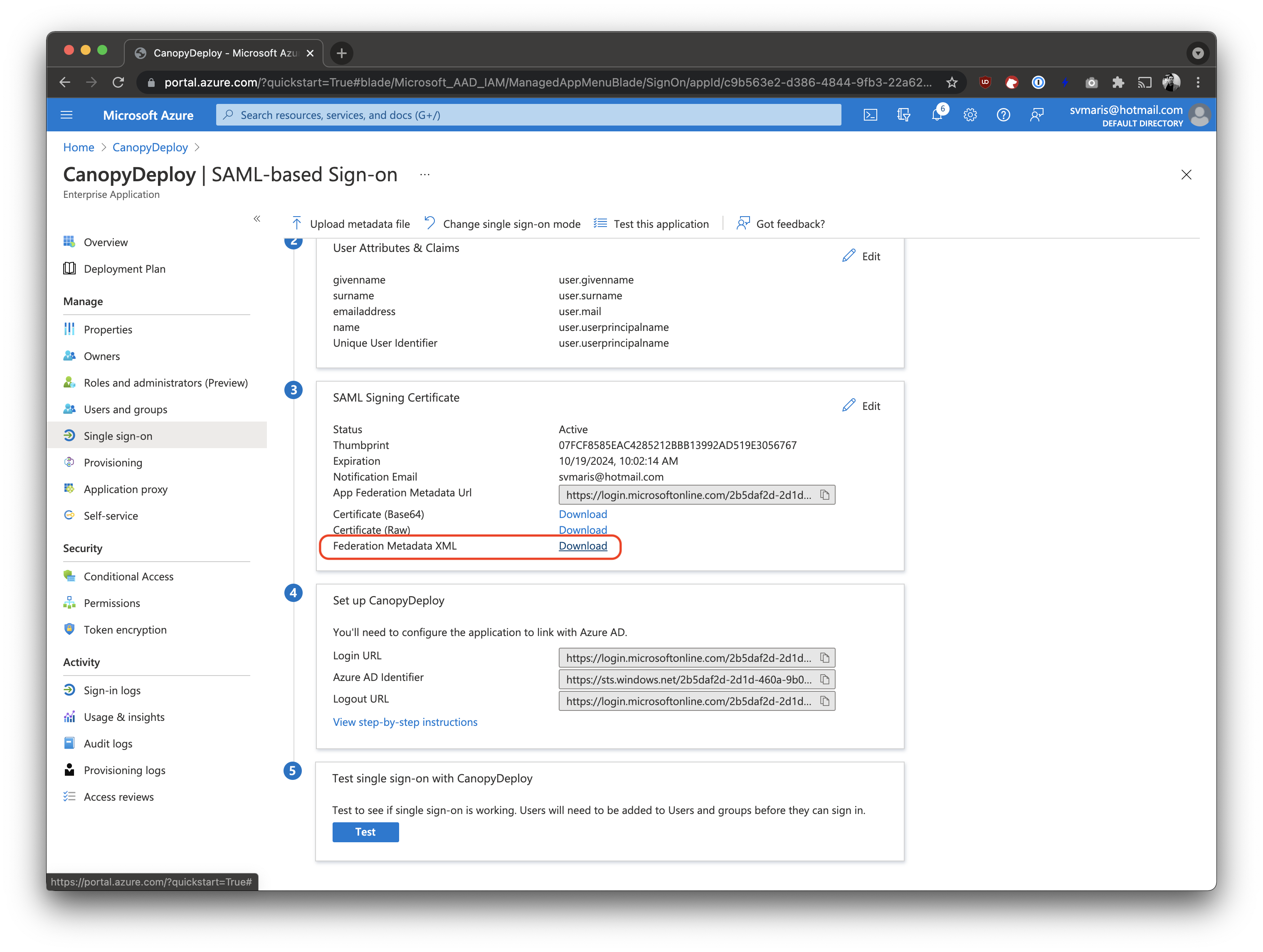
Then, after saving, download the Federation Metadata XML using the link in the SAML Signing Certificate box (step 3). This file contains the configuration of the identity provider for Deployteq. Send this file over to the support team of Deployteq.
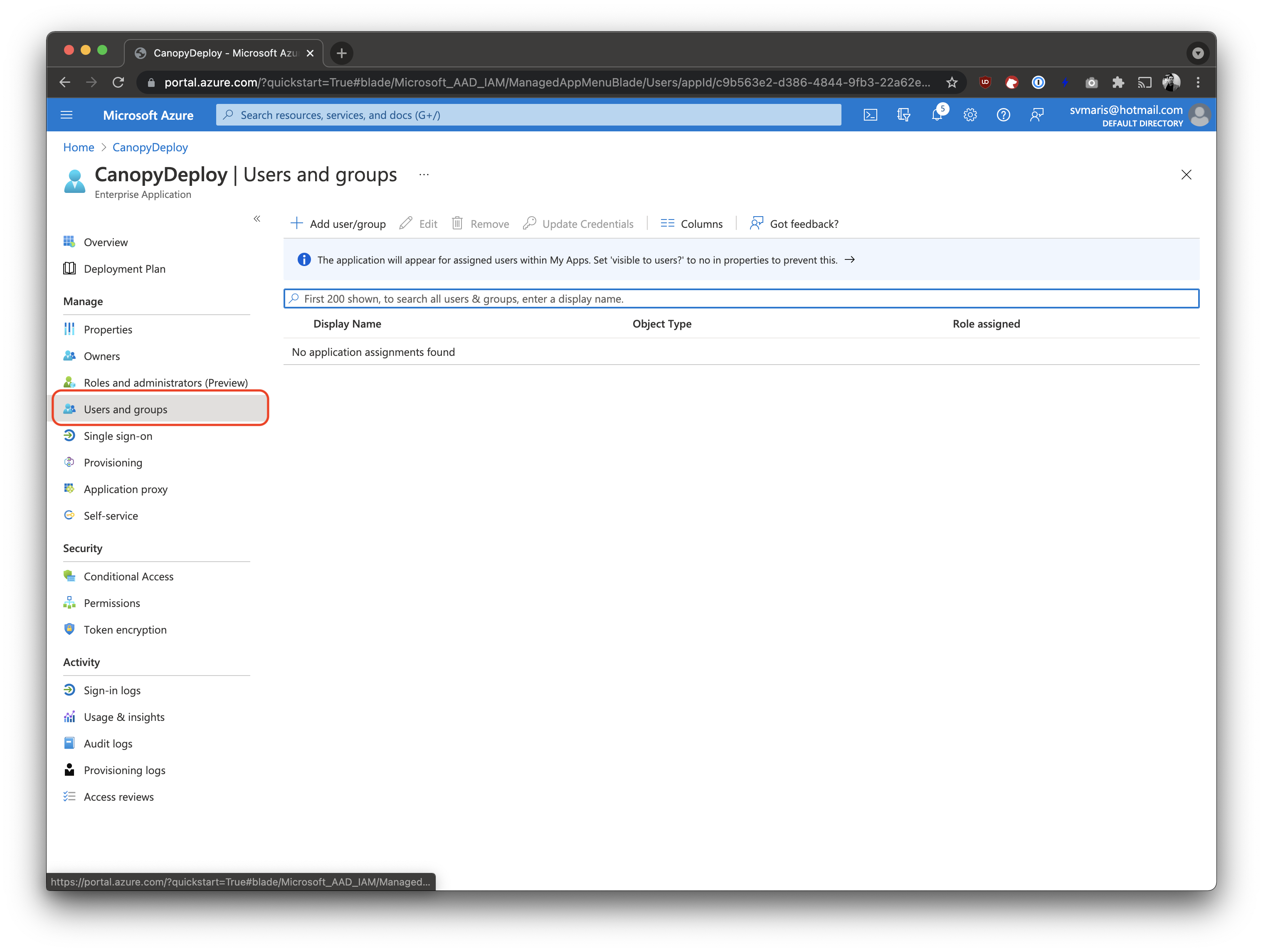
Assign Users or Roles to the Application
Click on Users and groups.
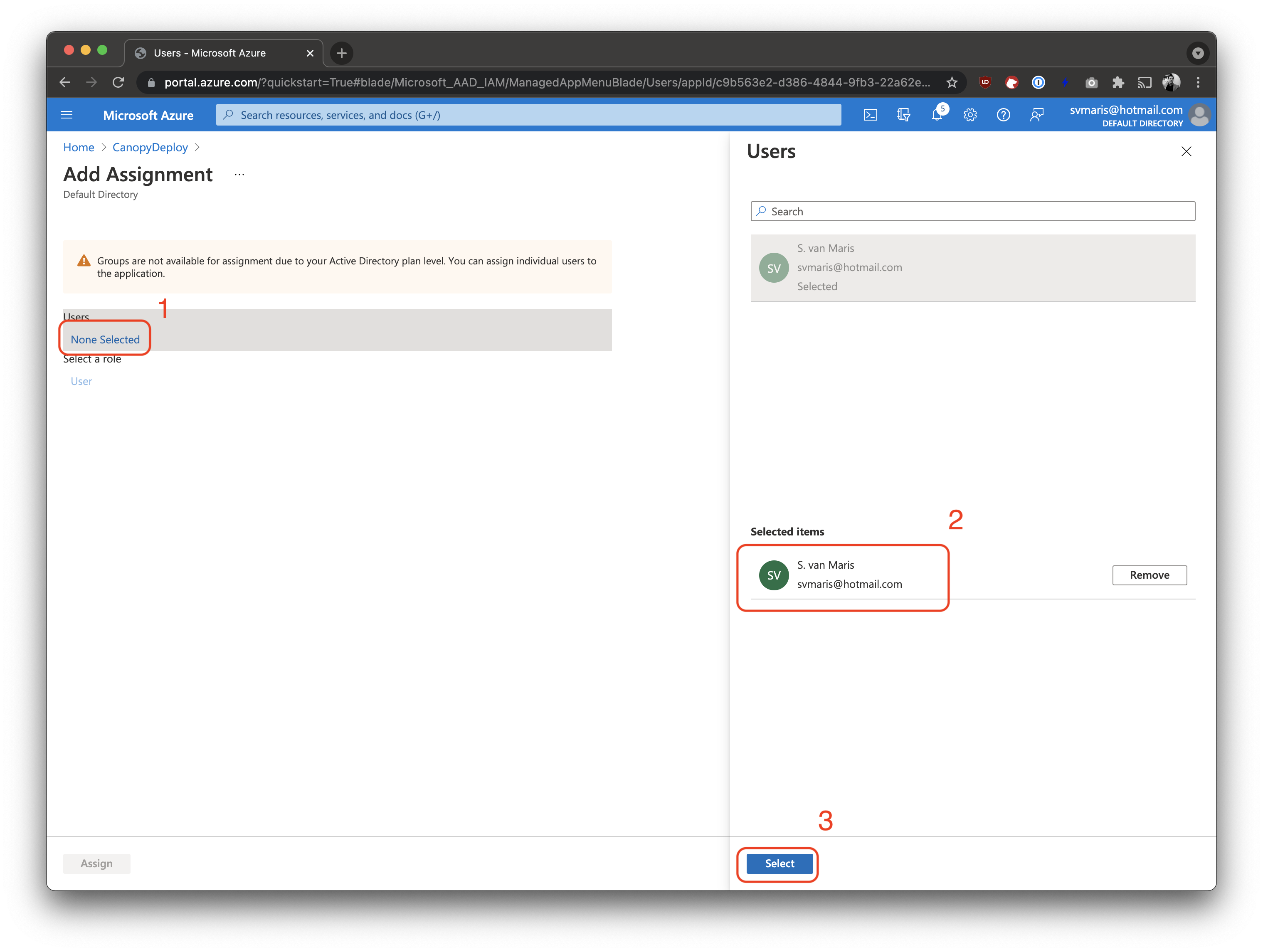
Add the users/roles that are permitted to use Deployteq.
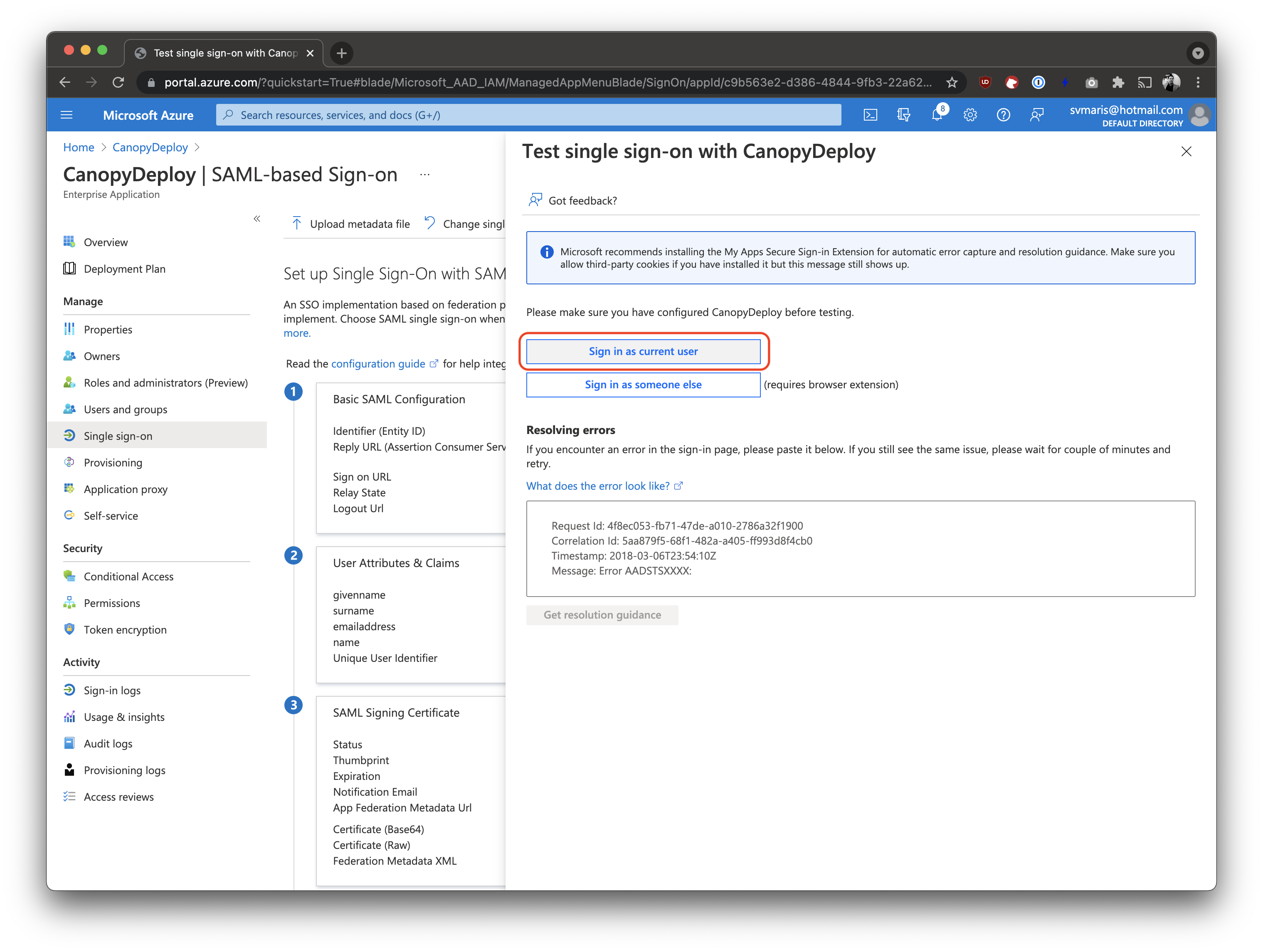
Test the integration
In the bottom of the screen, click Test. Then click between Sign in as current user.